Fedora
- 0 Posts
- 34 Comments
This page no longer exists.
What about
git add?
I worked on software that’s roughly as bug-free as a living bug. Intended behavior crashed the software. The master branch was broken, no way to compile the software without local changes. Devs hunted down suppressed exceptions to find out why everything crashes and burns on a daily basis. Unit tests are in the backlog, we’ll get around to it eventually.
Code reviews are ask whoever is available to approve your changes without looking at the code. Most seniors abused suppressed exceptions to use the Java Streams API, no proper technical justification. So my first official task was to unsuppress all exceptions. This caught many seniors off-guard, but made crashes infinitely easier to diagnose.
I would’ve done that even if it wasn’t my task. Shotgun debugging is hell. I don’t want to learn which component is most likely to fail silently due to retarded suppressed exceptions. Do your job properly ffs. Don’t shoot others in the foot. Don’t shoot yourself in the foot. You have absolutely no reason to shoot people’s feet. Stop it.
Java Applets!
I don’t know why this got downvoted. Google gives Mozilla a hefty paycheck to remain the default search engine on Firefox.

 7·8 months ago
7·8 months ago“What do you mean, tEcHnIcAl DeBt, CoDe MaInTaInAbIlItY? It works just fine. Get the feature done by Friday. Perfection is the enemy of progress!”
— A manager somewhere on planet Earth
What if we cannot afford the space of keeping everything backed uo forever?
You enforce a reasonable data retention policy, or charge for it.
What if it has been a year? Where do we put the limits to “okay, this is stupid” and “this is perfectably reasonable”?
If you fail to recover data for everyone, then the data retention is too low. If you succeed to recover data for everyone, then the data retention is too high. Pick a data retention policy that leans towards long enough that you can recover data for most people, or charge extra for it. It’s not that complicated.
What if the action cannot be reversed,
Tech support can reverse the action in this case, so I don’t see how this is relevant.
[…], and after deletion you need to anonimyze particularly sensitive data?
Most software doesn’t process credit card transactions, so I don’t see how this is relevant. Even if they did, they probably have to keep the data around due to regulatory requirements.
I say to all that, READ THE FUCKING MANUAL. If you are not apt enough to read and research about the software, you are not apt enough to use it.
People should at least try to make usable software first, but manuals are fine.
Same with hardware. You cut your finger because you didnt follow instructions clearly laid out for you not to cut your finger when using a saw? Maybe sawing was not for you mate
Yeah, shit happens, assuming they receive proper training and the saw complies with safety standards.
I feel like that anger should be directed at the people who made the software, not the people who use it.
The foolproof solution here is to… give people the option to restore what they deleted without contacting tech support. It’s obviously needed.
Nobody can expect anyone to read multiple warnings asking them if they’re really really sure whether they want to perform a reversible action they set out to do.
That’s a textbook example of a poor design that breeds more people desensitized to warnings.

 1·8 months ago
1·8 months agoI doubt they care about CT checks per se, they’re just afraid that Digicert fucking up will break their critical government services.
Right… uh. Listen, my government used a local/regional CA. Do you want to know what happened? My government got the privilege to emergency re-issue all of their TLS certificates with a different CA because the local/regional CA forgot to renew its own CA certificate. Everything was down. Government websites, government services, eID SSO authentication, etc. You had one job!
Gut-driven design. People could conduct usability tests, but neither their “data-driven” management, marketing, design, nor the development department care about that since it’s only “worthless” “additional” workload. Nevermind that usability testing reveals valuable insights about the people the business is supposed to generate value for. Or that usability testing identifies flawed designs before developers write any protoype code, designers draw sketches, etc. Or that usability testing nullifies unnecessary meetings about hypothetical scenarios littered with incorrect assumptions about reality. Usability testing is undervalued.

 5·8 months ago
5·8 months agoWhy would the secret services need a front company?
Governments here must use public tenders to buy services, and they pick the offer with the lowest price. Secret services can eat operational costs to place an extraordinarily competitive bid, but governments usually have anti-spying regulations. Hence, secret services bid with front companies.
But why bid in the first place, you may ask? eGovernment services are an attractive target due to the sensitive information at stake, and the potential to influence laws related to the eGovernment services. Secret services implement eGovernment services in a way that allows them to gain intelligence.
But how can they implement services in such a way, you may ask? Ask forgiveness, not permission. Of course, bullshit justifications play an important role here. E2EE? Why do that? Do you not want to scan files that go through the system for viruses? Real justification for why De-Mail stores sensitives emails in plaintext.
Governments now have the following options:
- Discard their paid work and forget about the initiative.
- Discard their paid work and contract someone more expensive than the original bidder.
- Pass laws to allow how the insecure service operates.
Remember De-Mail? Yeah, that exists. Exceptions that allow insecure storage of sensitive emails as long as it’s De-Mail. Exceptions that allow De-Mail providers to send legally binding emails on behalf of everyone. No, I’m serious. If anybody comprises De-Mail providers, they can practically send legally binding emails on behalf of everyone, as long as they don’t leave behind any trails of course.
But sometimes, like here I suspect, secret services hit the jackpot. They’ve got such an insecure implementation that the laws required to allow the service to operate nullifies the security of a large portion of the internet. Now, if enforced, they can intercept traffic like they used to back when everyone ran on http without the s. SIGINT is dead, long live SIGINT!
I’ll always appreciate Lisp for the most powerful REPL in existence of programming languages by a long shot. Name me one programming language that empowers developers to troubleshoot and fix runtime errors with high availability like Lisp does:
- Meh, who cares. Let’s continue to run.
- Here’s a REPL with the app state at the time of the runtime error. Happy debugging!
- Fix the bug in production inside of the REPL while everything continues to chug along.
- Save the changes to disk and check it into version control.
The REPL in Lisp is so powerful that there’s an entirely different approach to developing apps in Lisp. You can, and some do, code everything inside of the REPL. When they’re done, they save the file to disk.
I spent 7 hours to debug why doubles in Java classes brick my class file parser only to discover the following small print in the specification after I read the corresponding OpenJDK source code: In retrospect, making 8-byte constants take two constant pool entries was a poor choice. Yeah no shit. I chose to write a custom user stylesheet for Oracle specifications to enlarge notes since they’re obviously critical to the implementation of JVMs. I guess the technical writers at Oracle didn’t want to offend the developers who wrote the JVM originally at the expense of developers who write JVMs today.

 3·9 months ago
3·9 months agoIAbstractBlahBlahManagerFactoryControlBeansHandlerFactoryFactory

 9·9 months ago
9·9 months agoYes, it takes surprisingly long for the OOM killer to take action, but the system unfreezes. Just wait a few minutes and see whether that does the trick.
Linking to images should be illegal
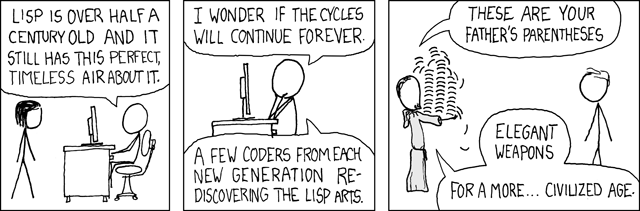
I see you’ve never used a Lisp REPL before.